Trezor Login – Secure Hardware Wallet Access Explained
This page provides a clear explanation of how Trezor Login functions for hardware wallet users. It describes what “logging in” means in the context of a Trezor device, how access is granted locally, and how device-based authentication ensures private keys never leave the hardware wallet.
What Trezor Login Really Means
Trezor does not use conventional usernames, passwords, or online accounts. Instead, the device itself is your login key. When connected to a computer, the Trezor hardware wallet allows local access to your digital assets by verifying your identity directly through the device. This approach removes the risks of centralized databases and stored credentials.
The device operates as a physical authentication tool. You confirm your access on the hardware wallet screen, making it impossible for malware or phishing websites to impersonate your credentials.
PIN-Based Local Authentication
The first security layer is your PIN code. When you connect the device, you are prompted to unlock it using a numeric PIN. The PIN is verified only within the device—it is never sent to the computer or stored externally. If the wrong PIN is entered repeatedly, the device enforces increasing delays to prevent brute-force attacks.
This PIN unlocks temporary access, allowing you to view accounts or perform operations. Once disconnected, the device automatically locks again, ensuring that no session remains open.
Passphrase: Optional Extra Protection
For users who require more privacy, Trezor supports an optional passphrase. A passphrase adds an additional secret on top of your recovery seed. Each unique passphrase creates a separate wallet, providing flexibility and plausible deniability. However, if lost or forgotten, the passphrase cannot be recovered—therefore it should be chosen and stored carefully.
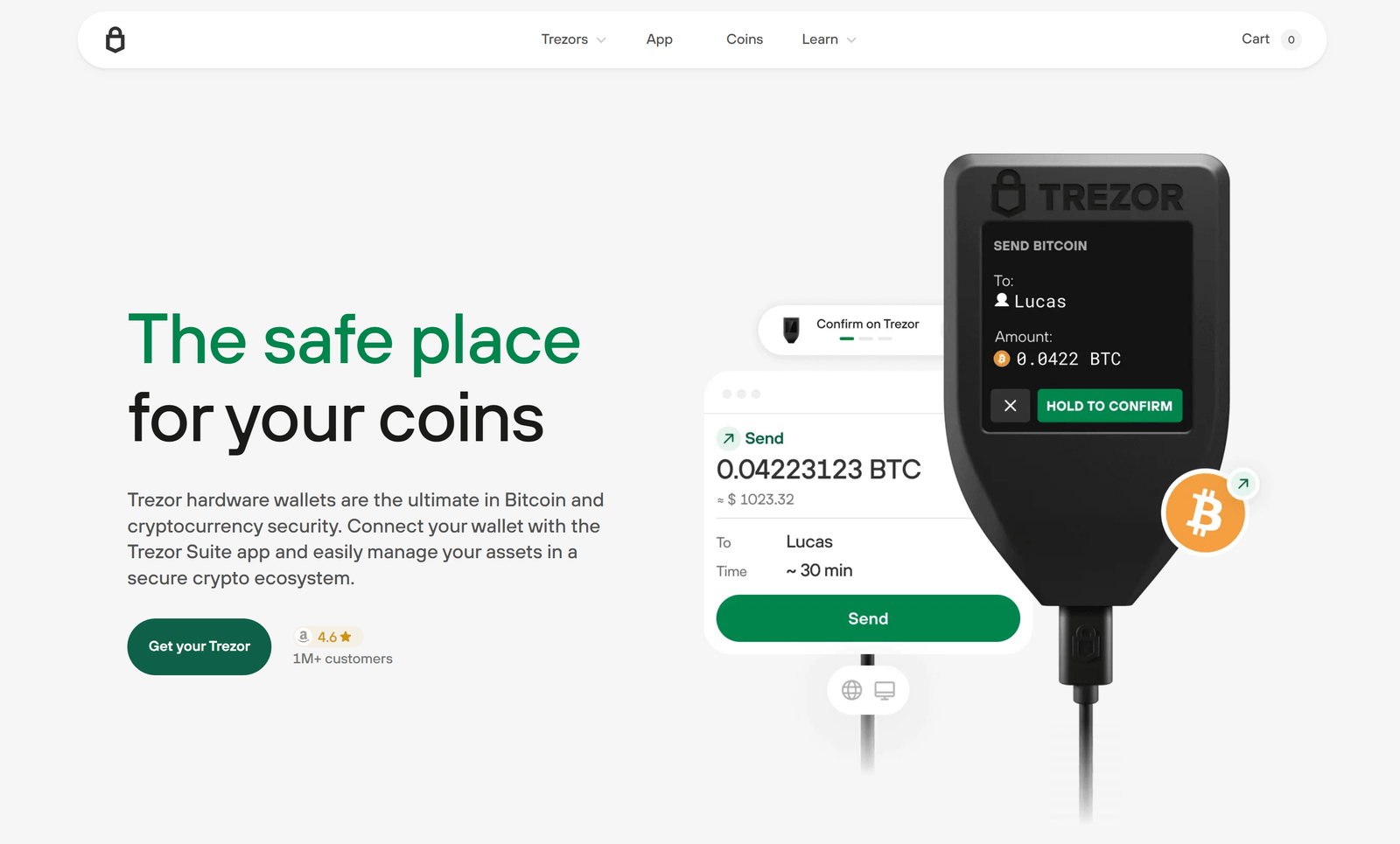
Device Confirmation for Each Action
Every sensitive operation, such as sending cryptocurrency or viewing a receiving address, must be confirmed directly on your Trezor’s screen. The device displays the transaction details, allowing you to verify them before you approve. Only after you confirm on the device will the transaction be signed and broadcast.
This approach guarantees that even if your computer is infected with malware, your private keys remain safe and unauthorized transfers cannot occur.
Hardware Security Principles
Trezor hardware wallets store private keys in an isolated chip designed to protect against extraction. The companion application merely serves as an interface to read public data and construct unsigned transactions. Signing occurs entirely within the hardware wallet itself, which means private keys never leave the device.
This architecture replaces remote logins with device-based authentication. You control access locally and confirm each action physically, reinforcing true ownership of your digital assets.
Recovery Seed and Wallet Restoration
During device setup, a recovery seed is generated—typically 12, 18, or 24 words long. This seed is your ultimate backup and should be written down and kept offline in a safe location. If your Trezor is lost or damaged, you can restore your wallet using the recovery seed on a new device.
Never type your recovery seed into any computer or website. Recovery should always occur directly through the hardware device’s secure environment.
Access Flow: A Simple Overview
- Connect your Trezor device to a trusted computer.
- Unlock the device using your personal PIN.
- Open your preferred companion application to view wallet balances.
- Review and confirm all operations directly on the device display.
- Disconnect the device when finished to automatically lock access.
This process represents the essence of Trezor Login—secure, local, and independent of online credentials or servers.
Troubleshooting Access
If your Trezor does not unlock or fails to communicate with your computer, check the USB connection, verify that your cable is functioning, and ensure your companion software and firmware are up to date. If you forget your PIN, you must reset the device and restore it using your recovery seed.
There are no vendor-controlled recovery methods or password resets, which protects users from remote access risks.
Security Best Practices
- Keep your recovery seed written down and stored securely offline.
- Use a strong, unique PIN code and never share it.
- Enable a passphrase only if you fully understand its security implications.
- Always confirm transaction details on the device screen.
- Update firmware through official channels only.
- Use your device on a malware-free computer.
How Trezor Login Differs from Online Accounts
Traditional online services manage user credentials on centralized servers. Trezor operates on the opposite principle: it never stores user data, passwords, or private keys on any external system. You hold complete control—and responsibility—for your hardware wallet and recovery materials.
In practice, “Trezor Login” means verifying yourself locally, using physical confirmation rather than trusting a remote authentication process.